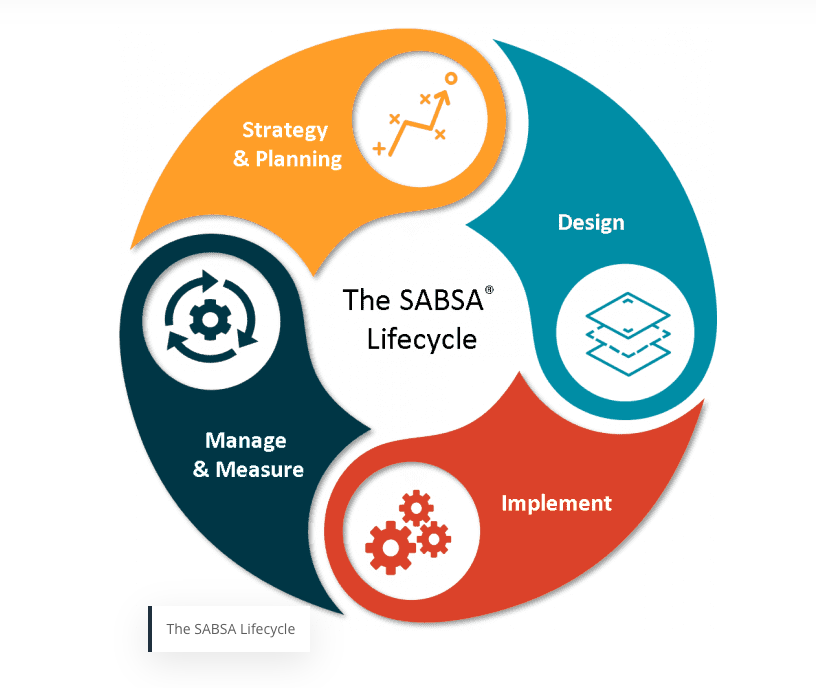
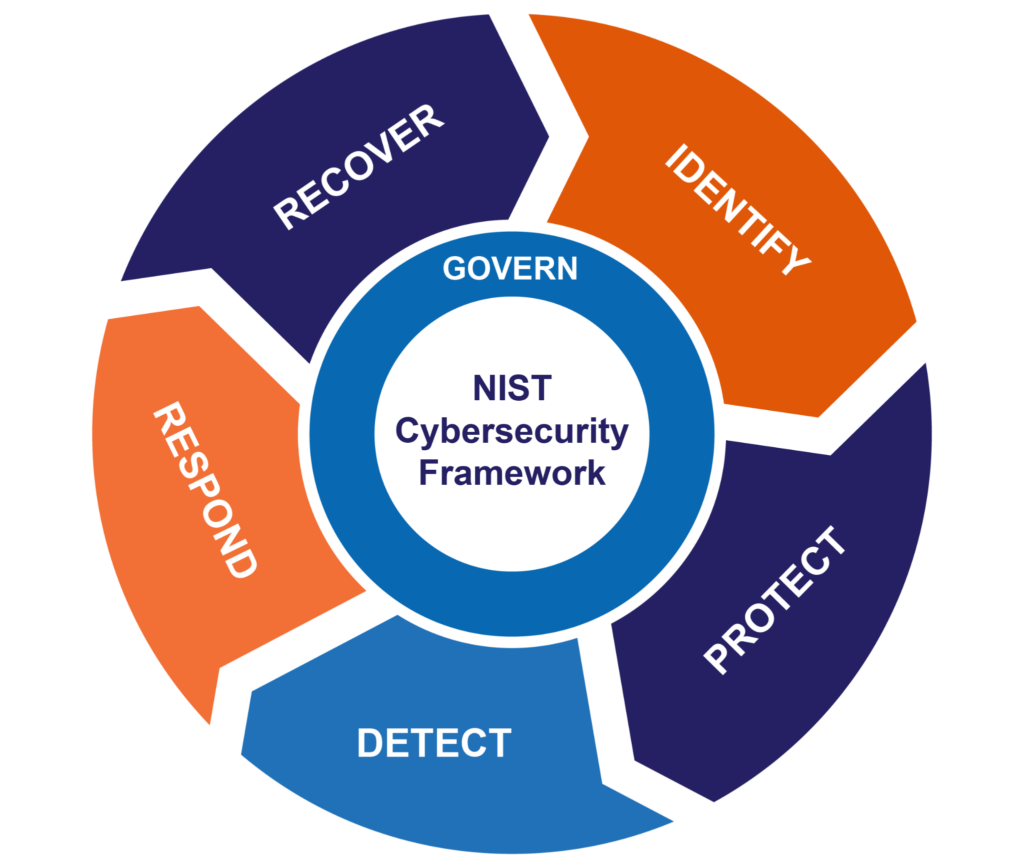
Enterprise Cybersecurity
Protecting Your Digital Assets
Comprehensive cybersecurity solutions powered by advanced AI and machine learning to safeguard your business.
Advanced Protection
AI-powered threat detection
Data Security
End-to-end encryption
Identity Protection
Zero Trust security
Why Choose Our Security Solutions?
- AI-Powered Protection
- 24/7 Threat Monitoring
- Compliance Ready
- Expert Security Team
- Rapid Incident Response